Assets, Threats, and Vulnerabilities
Assets, Threats, and Vulnerabilities
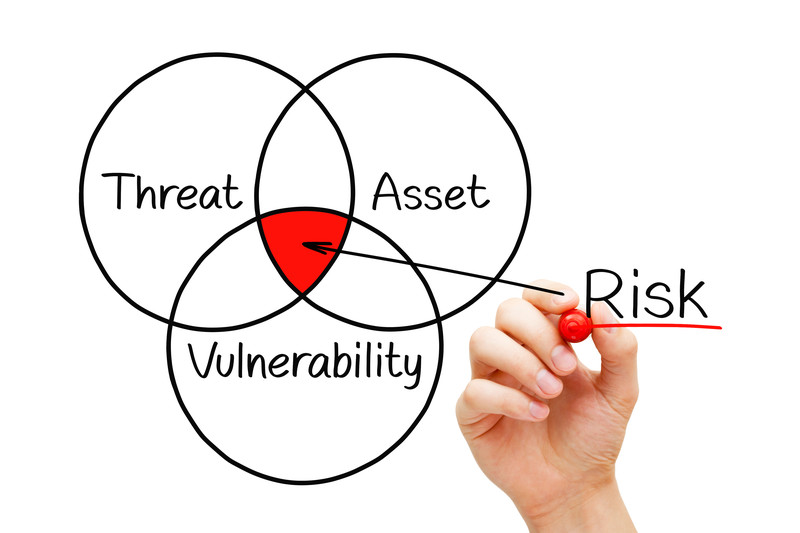
security risk planning consist of three main elements
1. assets 2. threats 3. vulnerabilities
security team help companies related to the risk,Security teams are responsible for protecting data in all states: in use, in transit, and at rest.
It's much easier to protect company assets if you know where they are and who's responsible for them.
Risk : anything that can impact the confidentiality , integrity , or availability of an asset.
Security Plans come in many shapes and sizes, but they all share a common goal: to be prepared for risks when they happen.
Security plans consist of three basic elements: policies, standards, and procedures. These three elements are how companies share their security plans.
A policy in security is a set of rules that reduce risk and protects information. Policies are the foundation of every security plan. They give everyone in and out of an organization guidance by addressing questions like, what are we protecting and why? Policies focus on the strategic side of things by identifying the scope, objectives, and limitations of a security plan.
Standards are the next part. These have a tactical function, as they concern how well we're protecting assets. In security, standards are references that inform how to set policies
A good way to think of standards is that they create a point of reference. For example, many companies use the password management standard identified in NIST Special Publication 800-63B to improve their security policies by specifying that employees' passwords must be at least eight characters long.
The last part of a plan is its procedures. Procedures are step-by-step instructions to perform a specific security task. Organizations usually keep multiple procedure documents that are used throughout the company, like how employees can choose secure passwords, or how they can securely reset a password if it's been locked. Sharing clear and actionable procedures with everyone creates accountability, consistency, and efficiency across an organization.
Compliance
is the process of adhering to internal standards and external regulations. In other words, compliance is a way of measuring how well an organization is protecting their assets.
CIA triad
Risk factors
there are two broad risk factors that you’ll be concerned with in the field:
Threats
Vulnerabilities
Assets
as business relay more on technology, cyber attacker doing more nasty work, security is team effort, as we are use to more technology and devices and more need security.
an asset is an item perceived as having value to an organization. This often includes a wide range of things. Buildings, equipment, data, and people are all examples of assets that businesses want to protect. Let's examine this idea more by analyzing the assets of a home. Inside a home, there's a wide range of assets, like people and personal belongings. The outside structure of a home is made of assets too, like the walls, roof, windows, and doors. All of these assets have value, but they differ in how they might be protected. Someone might place a lower priority on protecting the outside walls than on the front door, for example. This is because a burglar is more likely to enter through the front door than a wall. That's why we have locks. With so many types of assets to think of, security plans need to prioritize resources.
many varieties of assets that you could be looking into to protect, include IP, user data, employee machines, and to make sure you have a security posture that's on par with what you need.
Organizations protect a variety of different assets. Some examples might include:
Digital assets such as customer data or financial records.
Information systems that process data, like networks or software.
Physical assets which can include facilities, equipment, or supplies.
Intangible assets such as brand reputation or intellectual property.
asset classification
is the practice of labeling assets based on sensitivity and importance to an organization.
Common asset classifications
Asset classification helps organizations implement an effective risk management strategy. It also helps them prioritize security resources, reduce IT costs, and stay in compliance with legal regulations.Restricted is the highest level. This category is reserved for incredibly sensitive assets, like need-to-know information.
Confidential refers to assets whose disclosure may lead to a significant negative impact on an organization.
Internal-only describes assets that are available to employees and business partners.
Public is the lowest level of classification. These assets have no negative consequences to the organization if they’re released.
States of data : in use , transit , rest
Info Sec: is the practice of keeping data in all states away from unauthorized users. Weak information security is a serious problem. It can lead to things like identity theft, financial loss, and reputation damage. These events have potential to harm organizations, their partners, and their customers.
Understanding the three states of data enable security teams to analyze risk and determine an asset management plan for different situations.
Threats
Security teams can prioritize their efforts based on threats. In security, a threat is any circumstance or event that can negatively impact assets.Burglars aren't the only type of threat that affect the security of windows and doors. What if either broke by accident? Strong winds can blow the door open during a bad storm. Or, kids playing with a ball nearby can accidentally damage a window. If any of these thoughts crossed your mind
For example, an intentional threat might be a malicious hacker who gains access to sensitive information by targeting a misconfigured application. An unintentional threat might be an employee who holds the door open for an unknown person and grants them access to a restricted area. Either one can cause an event that must be responded to
Vulnerability
A vulnerability is a weakness that can be exploited by a threat, such as an unlocked door to a restricted area.Assets can have many different types of vulnerabilities that are an easy target for attackers.
A weak lock on a front door, for example, is a vulnerability that can be exploited by a burglar. And old, cracked wood is a different vulnerability on that same front door that can increase the chances of storm damage. In other words, think of vulnerabilities as flaws within an asset. Assets can have many different types of vulnerabilities that are an easy target for attackers.
For example, a technical vulnerability can be misconfigured software that might give an unauthorized person access to important data. A human vulnerability can be a forgetful employee who loses their access card in a parking lot. Either one can lead to risk.
NIST cyber security frame work
The NIST Cybersecurity Framework is a widely recognized and widely used set of guidelines, best practices, and standards for improving cybersecurity risk management in organizations. Developed by the National Institute of Standards and Technology (NIST) in the United States, the framework provides a structured approach for organizations to assess and enhance their cybersecurity posture. It was first published in February 2014 and has since become a cornerstone of cybersecurity practices for both public and private sector entities.The NIST Cybersecurity Framework (CSF) is a voluntary framework that consists of standards, guidelines, and best practices to manage cybersecurity risk. Organizations may choose to use the CSF to achieve compliance with a variety of regulations.
There are only three components core,tier, profiles.The core, tiers, and profiles. were each designed to help any business improve their security operations. Although there are only three components, the entire framework consists of a complex system of subcategories and processes
Components of the CSF
Core
Think of these categories of the core as a security checklist.
Tiers
The CSF tiers are a way of measuring the sophistication of an organization's cybersecurity program. CSF tiers are measured on a scale of 1 to 4. Tier 1 is the lowest score, indicating that a limited set of security controls have been implemented. Overall, CSF tiers are used to assess an organization's security posture and identify areas for improvement.
Profiles
The CSF profiles are pre-made templates of the NIST CSF that are developed by a team of industry experts. CSF profiles are tailored to address the specific risks of an organization or industry. They are used to help organizations develop a baseline for their cybersecurity plans, or as a way of comparing their current cybersecurity posture to a specific industry standard.
